Setup an IPv6 connection over IPv4 via Wireguard VPN (How to get IPv6 when you only have an IPv4 internet connection)
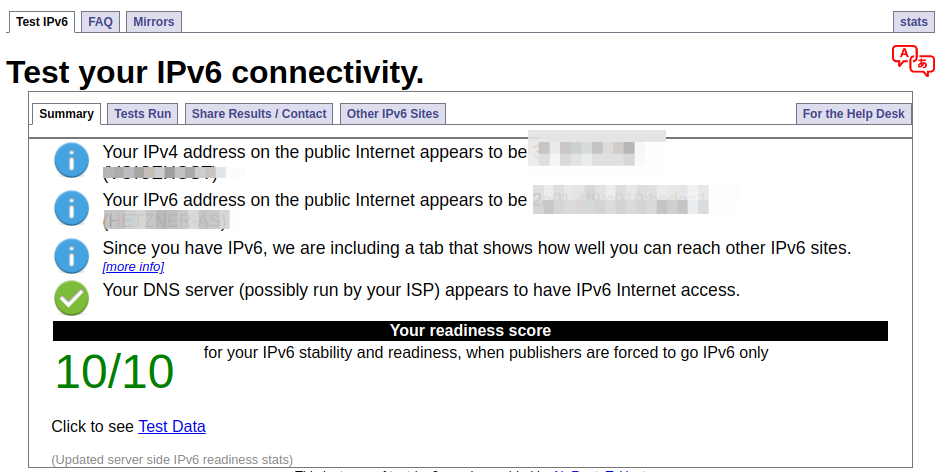
If you don't have IPv6 at home, sometimes you want to be able to test IPv6 only services- you need to tunnel a IPv6 connection somehow from your IPv4 internet connection to a server which does have IPv6 enabled.
You can achieve that by using a combination of:
- A cheap VPS server with IPv6 connectivity
- Wireguard
- Some iptables rules (in the Wireguard settings)
This example assumes an Ubuntu based system.
Easy to forget most examples you'll find online don't include the /sysctl conf changes needed, which are:
# Uncomment the next line to enable packet forwarding for IPv4
net.ipv4.ip_forward=1
# Uncomment the next line to enable packet forwarding for IPv6
# Enabling this option disables Stateless Address Autoconfiguration
# based on Router Advertisements for this host
net.ipv6.conf.all.forwarding=1
net.ipv6.conf.default.forwarding=1
Example server config:
[Interface]
Address = 192.168.7.1/32, fd42:42:42::1/64
#SaveConfig = true
ListenPort = 51820
PrivateKey = contents_of_file_privatekey
PostUp = ufw route allow in on wg0 out on eth0
PostUp = iptables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PostUp = ip6tables -t nat -I POSTROUTING -o eth0 -j MASQUERADE
PreDown = ufw route delete allow in on wg0 out on eth0
PreDown = iptables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
PreDown = ip6tables -t nat -D POSTROUTING -o eth0 -j MASQUERADE
[Peer]
PublicKey = contents_of_publickey_of_client
Example client config:
[Interface]
Address = 192.168.7.2/32,2a01:04f9:c010:beda:0000:0000:0000:0002/64
PrivateKey = contents_of_privatekey_of_client
#DNS = 2606:4700:4700::1112, 2606:4700:4700::1002, 1.1.1.2, 1.0.0.2
[Peer]
PublicKey = contents_of_publickey_of_vpn_gateway
Endpoint = <your-vpn-server-ipv4-ip>:51820
AllowedIPs = 192.168.7.2/32,::/0
Note the above hints at using Cloudflare for DNS should you wish.
How to start/stop wireguard
On both your server and client:
Start:
systemctl start wg-quick@wg0.service
Stop:
systemctl stop wg-quick@wg0.service
How do I ssh to an IPv6 server?
In the same way!
You might need to enable opensshd to listen on ipv6 though:
#...
ListenAddress 0.0.0.0
ListenAddress ::
#...Then reload sshd: systemctl restart sshd
Then to ssh into your server over ipv6 you can do ssh -6 root@<your-ipv6-address>
